Hi all:
Here is some more in depth info, for those interested.
And no, I did not run it, I scraped it.
Win32/Ska (Happy99.exe)
We have had a few queries about a virus (or worm) called Win32/Ska or
Happy99.exe. There has been a lot of
interest in this executable from the media recently (February 1999) because
of the capablilities of this virus
(dubbed a worm by some AV companies because of the way it spreads) which was
reputedly written by a
well-known virus writer called Spanska.
Win32/Ska is able to attach itself to SMTP e-mail messages and newsgroup
postings made from an infected
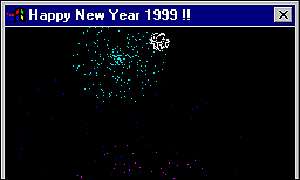
machine as an attachement called Happy99.exe. When the recipient runs the
attachement, a message "Happy New
Year 1999!!" and "fireworks" graphics are displayed on the screen:
<<happy99.jpg>> (This is a picture of it)
According to Network Associates (manufacturers of McAfee and Dr Solomon's AV
Software), when the Happy.EXE
is run it copies itself to Windows\System folder under the name SKA.EXE. It
then extracts, from within itself, a DLL
called SKA.DLL into the Windows\System folder if one does not already exist.
Although the SKA.EXE file is a copy
of the original it does not run as the Happy.EXE files does, so it does not
copy itself again, nor does it display the
fireworks on the users monitor. The worm then checks for the existence of
WSOCK32.SKA in the Windows\System
folder, if it does not exist and the file WSOCK32.DLL does exist, it copies
the WSOCK32.DLL to WSOCK32.SKA.
The worm then creates the registry entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\Ska.exe
="Ska.exe"
which will execute SKA.EXE the next time the system is restarted. When this
happens the worm patches
WSOCK32.DLL and adds hooks to the exported functions EnumProtocolsW and
WSAAsyncGetProtocolByName.
The patched code calls two exported functions in SKA.DLL called mail and
news, these functions allow the worm to
attach itself to SMTP e-mail and also to any postings to newsgroups the user
makes.
Network Associates say that they have discovered no destructive payload in
W32/Ska.
As always we would advise everyone that the best defense against this kind
of infection is never to run executable
attachments to e-mail messages or newsgroup postings unless you are
absolutely certain what the file is for and
what it is supposed to do, even if the message is from someone you know.
W32/Ska is detected and cleaned by Version 7.92 of WinGuard.
73's
Peter
[email protected]
|

